DASCTF2023二进制
careful
直接上传微步云沙箱
babyRe
调试一下了解主要逻辑:
v17的位置是处理输入字符串的;
StartAddress是最后进行比较的;
v17的位置的数据是经过前面有个函数异或解开的,带有一点混淆,处理后可以得到:
exp
1 | key = [ |
ez_exe
获取bin2
用pyinstxtractor生成pyc,再用pycdc反编译一下:
1 | import ctypes |
很明显,arr = range(len(file))() 和 open('bin1', 'wb').write(bytes(arr))是有些奇怪的,可能是无法彻底地反编译,于是用pycdas得到python字节码:
1 | b'bin1bin1bin1' |
可以使用dis来获取python字节码,但得使用python3.11版本:
1 | Disassembly of <code object <listcomp> at 0x00000160F71B8FA0, file "ez_py.py", line 59>: |
逆出逻辑,并将其改为bin2来解密bin2文件:
1 | from hashlib import md5 |
解密bin2
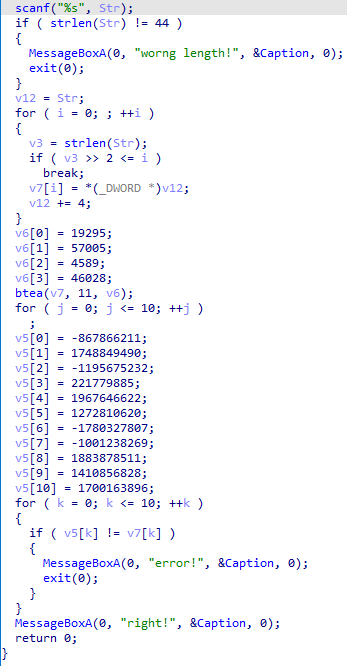
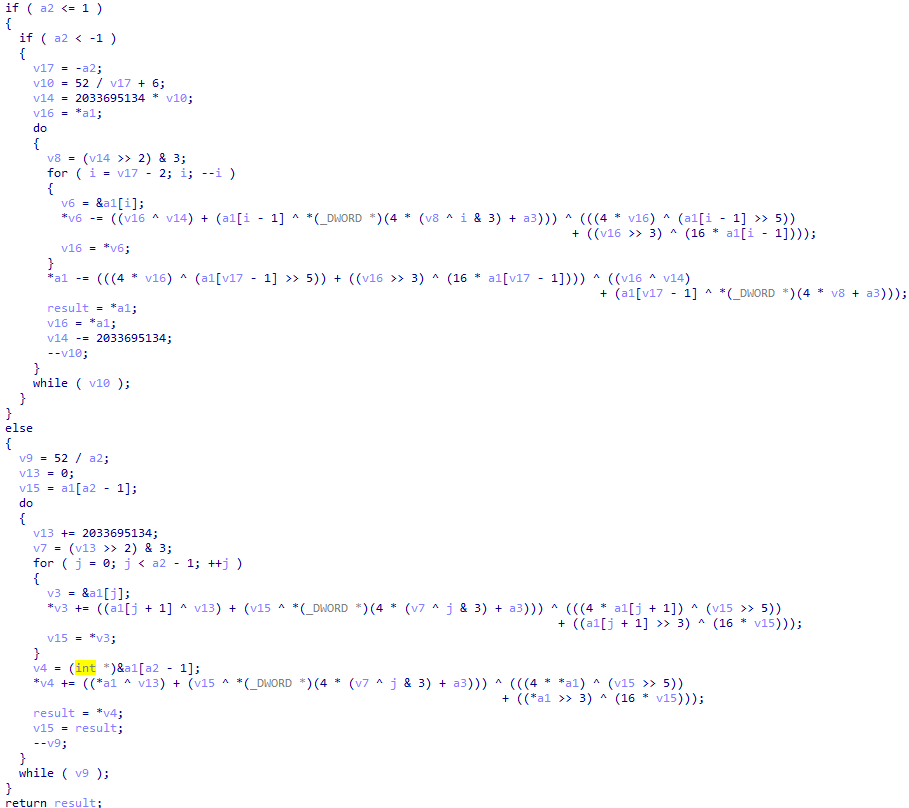
可以直接写脚本了:
1 |
|
cap
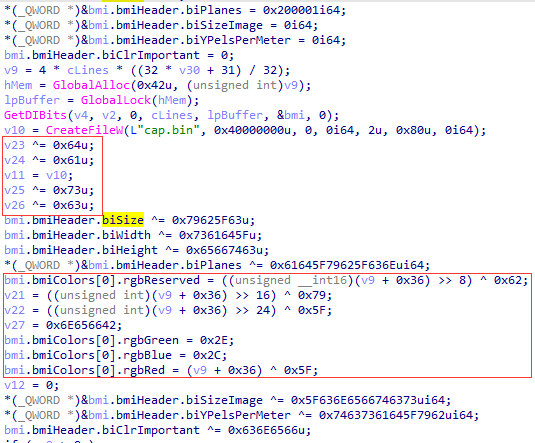
主逻辑:程序截图并进行处理保存为cap.bin。
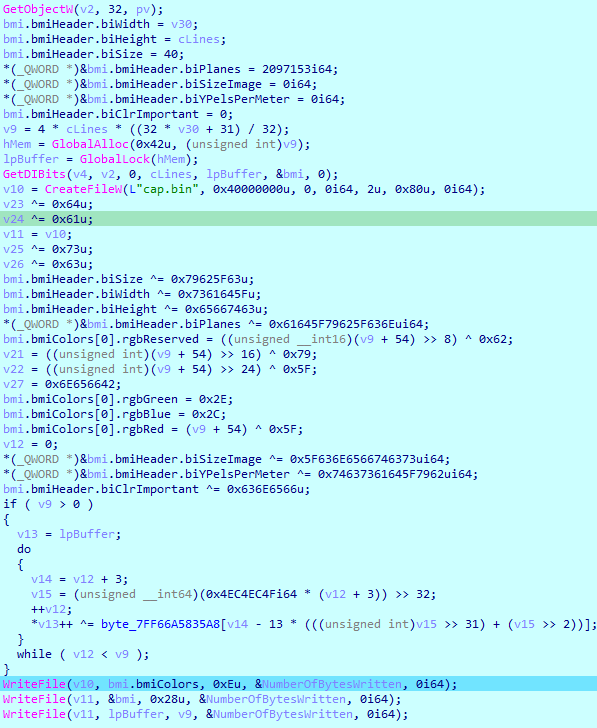
动态调试可得,
这部分处理bin文件的1-14个字节:
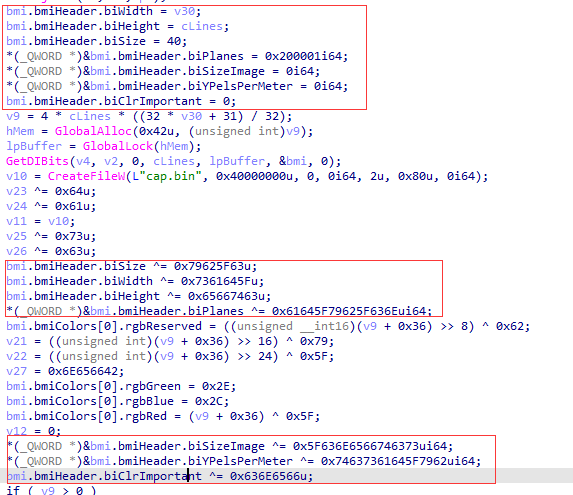
这部分处理bin文件的15-40个字节:
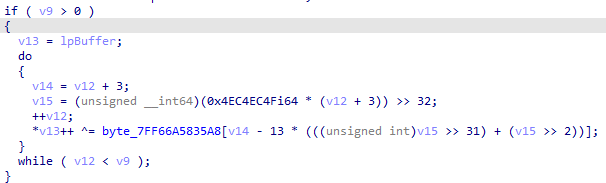
这部分处理bin文件的剩余字节,且下标起始于3:
exp
1 | def handle(a, b): |
unsym
这题还是我有点迷,看wp知晓流程:
- 输入密钥
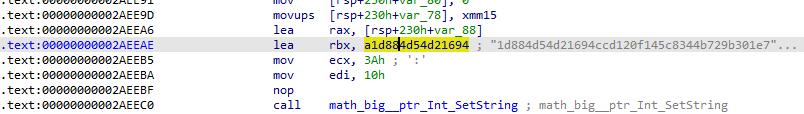
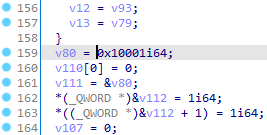
- 用RSA解密,n=0x1d884d54d21694ccd120f145c8344b729b301e782c69a8f3073325b9c5,e=0x10001,分解n,求出d
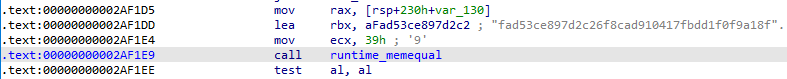
- 结果应该是0xfad53ce897d2c26f8cad910417fbdd1f0f9a18f6c1748faca10299dc8
- 将结果当作密钥和IV进行AES CBC模式解密解encrypted.bin
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 hahbiubiubiu!

